Web Application Scanning
- Home
- Web Application Scanning
Web Application Scanner- Smart, user friendly vulnerability management and threat assessment
Guardian1℠

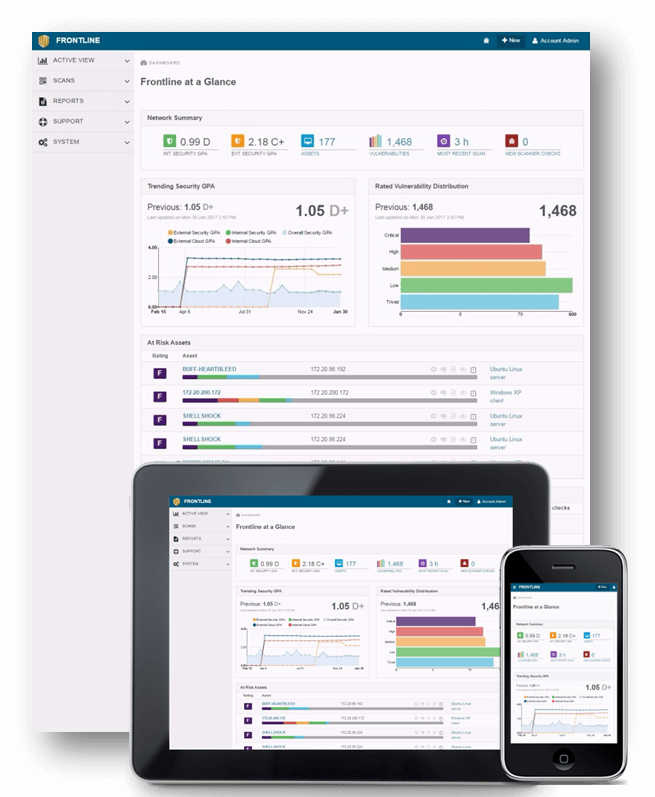
Assess Your Web Application Security
Web apps are attractive targets for malicious attackers due to the data they access and the transactions they execute. Organizations must always keep up with new standards and best practices due to the rapid changes in web application technologies. One thing hasn’t changed despite the prevalence of web-based assaults and the development of new web technologies: Constant security improvements to protect these apps is essential.
Guardian1℠ provides the best value for SMBs for testing dynamic web applications. You can rely on Guardian1℠ to give unmatched accuracy with little resource use thanks to our service-based approach
Quick, Comprehensive, Accurate
Although there are several web application scanning tools, they are difficult to set up and yield findings that are almost useless. Guardian1℠ offers technical advice to reduce or repair vulnerabilities, as well as insight into the security posture of the web applications used by your company.
"Blind Spot" Coverage
“Blind Spot” probes areas commonly missed by other web application assessment technologies and ensures visibility into vulnerabilities that could open the door to a breach.
Prioritized Vulnerabilities
Prioritization of the most critical vulnerabilities allows your organization to optimize its valuable resources through targeted remediation efforts.
Trending
Tracking and trending on new, recurred, and fixed vulnerabilities provides insight on the history and progress of your organization’s management of your web applications.
Robust Filtering and Reporting
Provides the data and views you need to instantly visualize vulnerabilities in your web applications, as well as on-demand report generation, including OWASP Top 10 reports.








